I have already explained to you what a VPN is and how it can protect you from data hijackers, snoopers, prying eyes and other cyberthreats from the Internet. Even geoblocking and censorship can be handled. We also know that a VPN is a logical connection between two devices. So-called VPN protocols such as OpenVPN are used for communication via these tunnels. So a VPN protocol is a method how a client connects to a VPN server.
Not all VPN protocols are equally secure or equally fast. I would like to introduce you to the most frequently used VPN protocols and describe their advantages and disadvantages.
A short analogy: We always talk about data traffic that flows over data highways. Just compare VPN protocols as such with the different cars on a highway. Some are faster or safer than others. With this picture in mind, the whole thing with VPN protocols is a bit easier to digest.
They all have one disadvantage! But advantages as well!
By the way, there is one disadvantage that all VPN protocols have. Your internet connection gets a little slower. This is simply due to the fact that there is another component involved in communication. The speed also depends on how fast or how busy the server of the VPN provider is. The encryption also eats up some of your device’s resources. Fortunately, modern devices and Internet connections are so fast that this disadvantage is not or very seldom of importance.
Of course, a big advantage of VPN protocols is that they encrypt your traffic. The internet provider or other prying eyes cannot spy on you. Especially if you use public Wi-Fi, hotspots and so on you get the most out of the advantages of a VPN protocol. But some have higher encryption than others and that’s why you should prefer them.
Bizarrely, using a VPN protocol could also make your Internet connection faster. Some internet providers slow down the speed depending on the traffic. They really do throttle! If you use a VPN, the provider can no longer see what you are doing on the Internet. That is why they are not able to classify your traffic.
TCP and UDP
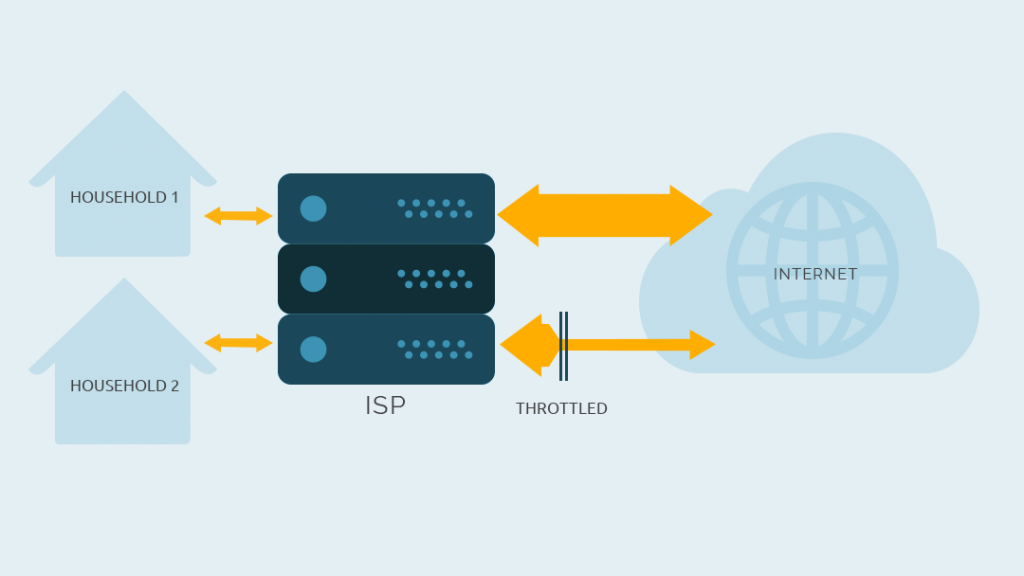
Before we get started with the protocols, we need to briefly explain the difference between TCP and UDP. Both can be found in layer 4 (transport layer) of the so-called OSI model.
TCP is the abbreviation of Transmission Control Protocol and UDP stands for User Datagram Protocol. UDP is the faster of the two protocols because it assumes a delivery. If a data packet is lost, the client does not notice this via UDP. This is useful for example for streaming media, VoiP (Voice over IP) and so on. It’s basically OK for all tasks where the loss of a packet is not critical or significant.
TCP on the other hand offers error correction and every packet is confirmed. The process is of course slower. The sender of a packet is waiting for an acknowledgment of receipt, if you will. If he does not receive it, the packet is sent again. You find more information and details about TCP and UDP in RFC 3366 if you are interested in the topic. There are enough cases where packets have to arrive and in those cases you use TCP.
As long as you don’t have any problems, use the faster UDP.
TCP and UDP communicate via ports
You can actually think of ports as numbered doors. You may know HTTPS from the address bar of your browser. This means that the channel is encrypted and normally HTTPS runs on port 443, while insecure HTTP is assigned to port 80 by default.
At IANA.org there is a list of standard ports. The ports are normally used in this way, but do not have to be. For example, the default port for the OpenVPN protocol described below is 1194, but the port may be blocked by a firewall. Therefore, some providers offer OpenVPN via port 443 or 53. These are the ports for HTTPS or DNS requests, and they will hardly be blocked.
OpenVPN – Open Source, secure and fast
OpenVPN is Open Source and something like the Swiss army knife among the VPN protocols. First, everyone can view the source code and the community makes sure that there is no backdoor. OpenVPN works with UDP and also TCP. That’s why this protocol is very flexible and depending on the application you can decide between reliability and speed.
Although OpenVPN is relatively new, the VPN protocol is very reliable and stable. It is considered to be very powerful and recommended as default by most VPN providers. OpenVPN is available for Windows, macOS, Linux, Android and iOS, among others.
The security protocol OpenVPN is based on SSL as well as TLS and encrypts with up to 256-bit.
Most clients and apps you can download from VPN providers use OpenVPN by default. Often you can choose yourself if you want to use TCP or UDP.
WireGuard – a promising VPN protocol
WireGuard is the latest VPN protocol and is currently still in a development phase. The focus is on simplicity and currently the whole code has only 4000 lines.
In the end, similar to SSH, keys are exchanged and thus the secure tunnel is established. The connection is very fast with WireGuard and the VPN protocol can roam. I was allowed to try the early WireGuard implementation of NordVPN and it worked great already. I jumped from one WLAN to another and even switched to a mobile data connection. The tunnel was up and running again without interruption. This is really fun, even if the protocol has disadvantages.
Meanwhile, the WireGuard protocol has arrived at NordVPN and has been incorporated into the Linux client. It is called NordLynx and speed tests shows that it is faster than OpenVPN. It’s working great on a Raspberry Pi by the way!
Get NordVPN for your Raspberry Pi!*
The latency is lower than with OpenVPN and so far I can’t see any disadvantages. If there is no massive security problem, I see WireGuard as the VPN protocol of the future. NordVPN (big discounts NOW)* is offering WireGuard in its Linux client, as already mentioned. It’s not quite clear yet when other major VPN providers will introduce WireGuard. But quite a few have already mentioned that they are looking into it.
The Linux client of NordVPN works great on the Raspberry Pi by the way. Now you can use your SBC with the fancy new VPN protocol. It works really great!
SSTP (Secure Socket Tunneling Protocol) – VPN protocol for Windows
SSTP is a method to transport PPP traffic over SSL/TLS. The VPN protocol runs by default on port 443 and is harder to block by a firewall than others. SSTP is considered to be similarly secure and good as OpenVPN, but there is a small catch.
Microsoft owns SSTP and has also developed the VPN protocol. So it is proprietary. The advantage for Windows users, however, is that the client is implemented by default starting with Windows Vista SP1. If you don’t want to use the client of the VPN provider and configure a VPN connection manually, you don’t have to install any third-party software with modern Windows versions.
There are also SSTP implementations for Linux and macOS, which work well in my experience. If you use Ubuntu or a distribution based on it like Linux Mint, you can simply install the SSTP client via PPA. Mac users can try their luck with iSSTP. For Android I recommend the SSTP VPN client. The software is not free but it’s not expensive either. The good thing is that it doesn’t need root access and, unlike all the other free solutions, works really smoothly.
Furthermore, SSTP runs via TCP and is therefore slower than a UDP connection. There could be problems with the so-called TCP meltdowns. If that happens the connection will be very slow, simply put. But as I said, almost every firewall can be bypassed and you can almost always establish a VPN connection. In fact SSTP has helped me out several times when OpenVPN and other protocols were blocked. Alternatives are always a nice to have. With enough options we can outsmart the censors.
PPTP is considered an insecure VPN protocol
PPTP (Point-to-Point Tunneling Protocol) is the oldest VPN protocol and has been used since Windows 95. Since 2012, however, PPTP has been proven to be no longer secure. PPTP is very fast, but with modern computers the encryption can be cracked quite quickly. Since PPTP was developed for much older hardware or CPUs, the protocol also runs well on old devices. If it is not about sensitive data, but for example about streaming video and audio, PPTP is still an option.
PPTP is also available for almost all operating systems. In Android it is implemented by default, in modern Linux distributions as well and in Windows anyway. In some situations PPTP is still better than no VPN at all!
Just remember: If it is not absolutely necessary, do not use PPTP under any circumstances.
It is fast, but also very insecure.
L2TP / IPsec
L2TP and IPsec actually belong together, because they are only used as a combination in the VPN world. You can use L2TP to tunnel all protocols that can be encapsulated in PPP. But the problem with L2TP is that it does not offer any security. This is of course not very good.
That’s why L2TP is tunnelled through IPsec and therefore the necessary security is provided. IPsec can only tunnel IP packets and neither DNS nor IP address can be configured. But if you combine everything you can. The two protocols iron out their weaknesses and the combined use of both protocols results in a reasonable solution.
L2TP over IPsec is considered to be as secure as OpenVPN, but less flexible. For the desktop operating systems Windows, macOS and Linux you get software that can use L2TP over IPsec. But if OpenVPN or WireGuard should work, take one of those instead.
For mobile devices I have good news. Google’s Android and Apple’s iOS allow dial-up via L2TP over IPsec by default. So you don’t have to install anything. Most good VPN providers offer apps, so you don’t really have to worry about this. Just keep it in mind in case you need the combination L2TP over IPsec at some point.
IKEv2
IKEv2 or Internet Key Exchange version 2 was jointly developed by Microsoft and Cisco. Mostly it is used just like L2TP with a protocol for authentication like IPsec. The protocol supports EAP (Extensible Authentication Protocol), pre-shared keys and digital signatures.
The IKEv2 protocol is considered a good compromise between security and speed, and offers very high encryption. More precisely, this is AES 256-bit for data and SHA256 for control messages.
It also supports the MOBIKE protocol (Mobility and Multihoming ). If networks change, your VPN will notice this and reconnect immediately. You can compare it a bit with the kill switch that good VPN clients offer. It immediately deactivates all network lines if the connection to the VPN server is interrupted.
In newer versions of Windows (starting from 7), macOS and iOS IKEv2 is implemented by default. Some manual work is necessary for the configuration. If VPN providers support IKEv2, instructions are usually available on the provider’s website.
If you want to use IKEv2 on Android, you can install the strongSwan VPN Client. The software is also available for Linux, but if you want to configure it you have to use the command line. IKEv2 is also compatible with Blackberry devices.
A disadvantage is that IKEv2 uses certain port (500 and 4500). If a firewall blocks the port a VPN using it won’t work.
There is nothing wrong with using IKEv2. In case it doesn’t work you can still try OpenVPN or WireGuard.