A VPN or Virtual Private Network is a direct connection between two networks via a public connection such as the Internet. In order for me to explain to you exactly how a VPN works, a few short and simple basics are necessary. Don’t worry, I will keep it understandable.
How do I connect to the Internet?
I just assume that you have a router like a Fritz!Box for example. This device is your gateway to the Internet. The gateway to the Internet has an internal IP address and an external. The latter is assigned by your ISP (Internet Sevice Provider). It is accessible from the internet. The internal IP address is the gateway that I have already mentioned. Your computer, smartphone, or tablet is connected to the router and therefore uses the internal IP address. The connection is either via wireless LAN (Wi-Fi) or a network cable. It communicates via the external IP address with the ISP and this is how you browse the Internet. It does look like this.
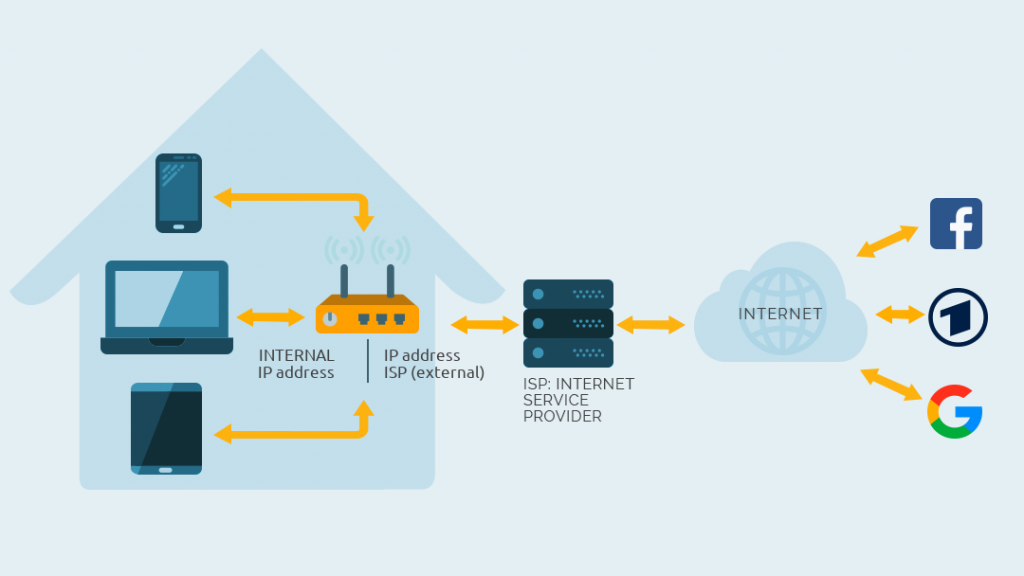
When you visit a website or use a service on the Internet, it looks as if all your devices are coming from the external IP address. But the router knows which device made which requests and distributes the packets accordingly. We call this NAT (Network Address Translation), but you don’t have to remember that.
The Internet Service Provider may log your data
Since all packages are sent via the Internet Service Provider, this company can log your data and assign it to your name. After all, the ISP knows when you have which IP address. In the USA the Internet Service Provider is allowed to make money out of such data and sell it! Fortunately this is not yet the case in many other countries like Germany.
However, the legislator can demand the release of sensible data. The ISP knows which websites you visit, whether you download torrents, use P2P (peer-to-peer) file sharing and so on. If you visit encrypted sites and use encrypted services, the ISP will not be able to read the data. However, they will know that you are using the services.
Tip: Torrents and file sharing may be illegal, but don’t have to be. In any case, it’s nobody’s business what you do on the Internet, is it?
The ISP and censorship!
If you use the standard connection of your provider, you usually use their DNS servers as well. With DNS and other methods the provider can censor websites and services. You will be amazed, but there is Internet censorship in Europe, too. In Great Britain, for example, ISPs block various illegal torrent portals. Just have a look at the OONI Explorer to see who censors what. Europe, of course, blocks a lot less websites than in China, Russia, North Korea or Egypt. But we are not free from internet censorship either! In Germany the government discussed a blocking list — the so-called Access Restriction Act., what is actually directed against child pornography. That looks initially like a good thing.
BUT! Similar laws exist in other countries and blocking lists have appeared on WikiLeaks (for example the one from Denmark) with other websites as well. The respective legislators have apparently extended internet censorship at will. By the way, the Access Restriction Act has never been applied in Germany, but discussions like that will never stop. We could discuss the topic for hours, but that would go completely beyond the scope of this article. The fact is that states, governments and authorities would prefer to censor and monitor at will and as they please. In Germany the BND (Federal Intelligence Service) is sniffing at the De-Cix by the way, one of the world’s largest Internet hub. The arguments for this are mostly flimsy and implausible. The prying eyes of other secret agencies I don’t have to mention, do I?
A VPN protects us in almost all areas
This is where a VPN comes into play and we clarify the question: What is a VPN and how does a Virtual Private Network protect us?
If you use a Virtual Private Network, you connect to another computer via a secure line, also called a tunnel. For websites and services on the Internet, it looks like you are visiting using this other computer. Basically you move your NAT router to another computer. Your ISP can see that you are connected to the other computer. But the company can’t see what data you are transferring. The tunnel encrypts our connection. You are now using the IP address of the computer you have dialed into. Your own IP address, however, is obfuscated or masked.
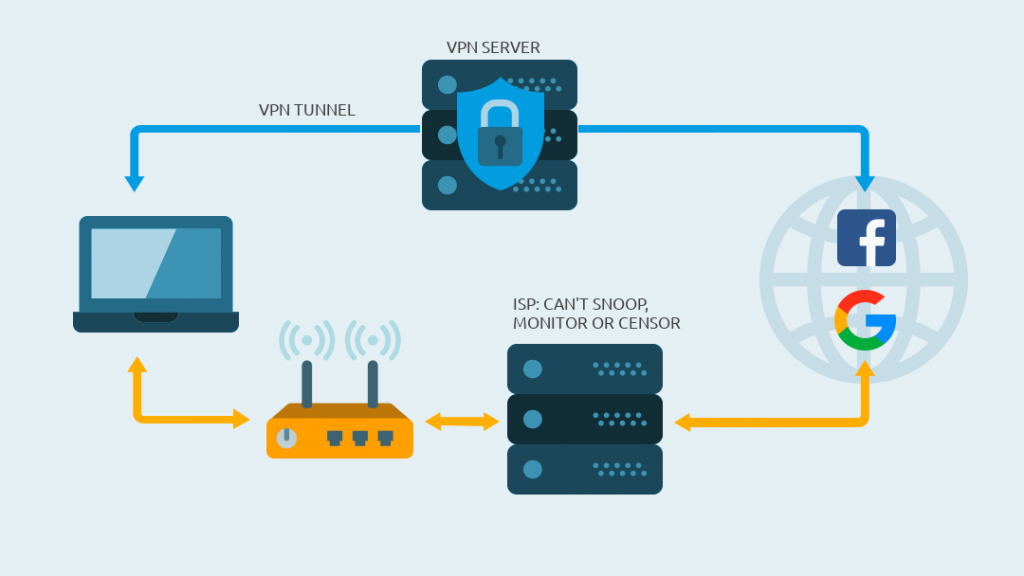
Of course, you also bypass the internet censorship of your ISP or a government! That’s why governments don’t like VPNs, because you avoid control and circumvent surveillance.
Good VPN providers such as NordVPN (big discounts NOW)* or [AirVPN] offer servers in many different countries and cities. So you can choose a virtual location and it looks like you are using the internet from there.
So the Internet Service Provider cannot read the data at all? Really?
That actually depends on how strong the encryption is and which VPN protocols you are using. The topic of cryptography and encryption is very complex. I try to explain it as simple as possible.
Good VPN providers encrypt with AES-256 (Advanced Encryption Standard). This is a key with 256 bit. In other words, there are 2256 or 1.1 x 1077 different combinations of how the cipher could look like. Still sounds possible? OK, let’s write down the possible combinations as a number: 115.792.089.237.316.195.423.570.985.008.687.907.853.269.984.665.640.560.000.000.000.000.000.000.000.000
If I want to break such a key, the only way I can do it is a so-called brute-force attack. I would have to try every single combination until I get the right key to decrypt the data. A Raspberry Pi would calculate for a while – joke aside. Modern supercomputers would need billions of years to crack such a key.
But the so-called quantum computers could mess up the cryptographic sector. Thanks to the Shor algorithm, attacks on the key could be carried out in polynomial time and the process is theoretically much faster.
However, it has not yet reached that point and the currently high-quality encryption methods are considered secure. As soon as the quantum computers are a problem, I scream very loudly and warn you. Of course, the other side is not sleeping either and cryptography experts are already dealing with encryption in the age of quantum computers. This is called post-quantum cryptography. Our crypto masterminds will have us covered here – I have no doubt on that.
Can the ISP monitor the VPN server?
Yes and no. If the same telecommunications company operates your Internet connection and the dial-up server of the VPN provider, it would theoretically be possible. Of course, this is also possible if the ISPs exchange data. But it is very unlikely.
Furthermore, you will get lost in the crowd as different people are using the VPN at the same time. This contributes to anonymity and your identity is hidden like your IP address.
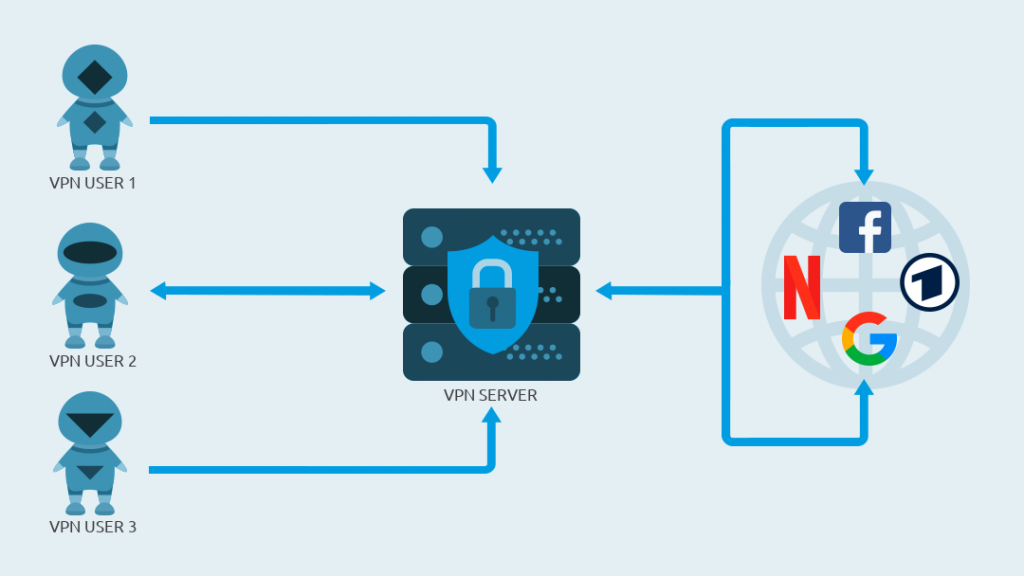
Let’s put it this way: In theory, everything can be monitored, but with a VPN it becomes much more difficult for prying eyes.
But the VPN provider has access to any data, right?
In theory, yes. But that is exactly what serious VPN providers won’t. Many even have a strict zero-logs policy. The companies promise, that the store absolutely no data concerning traffic and DNS requests. But that doesn’t mean that the store or monitor no data at all. But most VPN providers only log the most necessary data. Otherwise, they could not determine, for example, how many devices you have connected simultaneously. However, the trustworthy providers delete data like immediately at the end of your session. If you read zero-logs you should treat it with caution. I just wanted to mention that.
Some providers have their headquarters in countries where there are no laws for data retention. Firstly, the nosy governments have no control over the VPN providers and secondly. If there is no data the VPN providers can’t give it away. NordVPN for example is working on a technology that the operating system and all sensible data is only kept in RAM. As soon as the server is switched off that data is gone. Even if the government seizes a server, they can’t extract data from the server as soon as they move it.
Ideally your VPN provider is located in a country that is not part of the 5/9/14 eyes alliance.
Is a VPN useful elsewhere?
Oh yes! Whenever you are on the road and use a foreign network a VPN protects you! I am talking here about public hotspots, Wi-Fi access points and so on. You don’t know who set up the network and whether the owner is sniffing data.
In this case it is very useful if you establish an encrypted connection to a server of your VPN provider and access the Internet via tunnel. The owner of the network can’t snoop.
I can think of so many more examples. Airbnb, train, airports, Wi-Fi in a café and so on. A VPN is very useful if you are on vacation. Are you travelling and using the Wi-Fi in a hotel or at the airport? -> Not without VPN!
Does a VPN only protect against data collectors?
Some VPN providers offer apps that block ads, trackers and so on. A lot of companies try to collect data about you via Internet. Advertisers use this data for example to show personalized ads. It doesn’t really matter if it’s Facebook, Google, Amazon or anyone else — data is the new gold. For example, if you use different devices in the same household through the same router, Google or Facebook will know that they are all on the same network, including relatively accurate location information. It sounds scary but the big companies analyze data like that nowadays. The keyword here is Big Data.
Governments are already discussing the possibility of selling data. Although anonymized, in the age of Big Data, with enough data it would be possible to draw the right conclusions. This is not a conspiracy theory of mine while I am wearing my tinfoil hat — it is possible. That’s why you want to make things as difficult as possible for the data collectors and protect your privacy as much as possible.
Router hacks and DNS poisoning
Furthermore hackers hijack routers again and again. Part of the problem is that the manufactures don’t support the devices long enough and provide important security updates. Using so called DNS poisoning, attackers redirect you to fake and malicious websites, display advertisements, distribute malware and so on. A virtual private network helps in this case because you normally use the DNS servers of your VPN provider. These are usually considered secure. A good VPN provider has a security team that takes care of such things. The café around the corner will not be able to afford such a special team.
In your network at home you could also protect yourself with projects like Pi-hole. This blocks most trackers and so on. A combination of Pi-hole and VPN would also be possible, but you have to be careful not to create a DNS leak. You would practically have to tell the Pi-hole to use the DNS server of the VPN provider.
The thing with the location — can I use a VPN for geoblocking?
Yes, you can. Geoblocking or geographical blocking is a real disease, but it has something to do with licenses. In other words it’s all about money. In the end, it’s also a form of regional censorship. If a service is geoblocked, you can only use it with an IP address from a certain region.
An example: ITV streams a football or rugby match and of course you can watch the event in the UK. But if you are abroad, you will receive an error message that the desired program is not available.
If you are travelling and still want to watch Netflix, Eurosport, Amazon Prime or the UEFA Champions League and so on, this usually works with a VPN. You dial into a server of your desired country and start watching. In other words, with a VPN you beat geoblocking. Streaming providers actively fight VPNs, but it’s a cat-and-mouse game. And to be honest — if you are on holidays you shouldn’t watch TV anyways. 😉
In the EU the stupid Geoblocking has been partially abolished since March 1st 2018. This only applies to commercial services like Netflix, Amazon Prime and others, if the customer is temporarily in another EU country. Free media libraries like those of ARD and ZDF are not included, however. Geoblocking really is a pain in the ass if you excuse my French. But we know the cure! With a VPN I have always been able to get to the shows and live events I wanted to see!
Even if it’s not about geoblocking, you want to protect your privacy when you travel, right?
Providers around the globe throttle the speed – net neutrality
But there is more to the story. Providers around the globe throttle certain internet traffic. I’m sure you’ve heard the discussion about net neutrality. Net neutrality means that all traffic is treated equally. If the ISP can read the traffic, it is able to prioritize or throttle the traffic. This means that ISPs priorize certain services or applications and slow down others.
It depends on the countries or providers how they regulate this. It’s not the same everywhere. In the USA, net neutrality is in limbo. There is resistance, including from the EFF (Electronic Frontier Foundation), but it is not yet clear whether it will be successful. Of course, the reason here is money. Those who pay get access to the data highway. The others share the slow lanes. There is a great concern that the move could end up in a two-tier Internet. In this case some data will be delivered on paid fast lanes and other data has to take bumpy road.
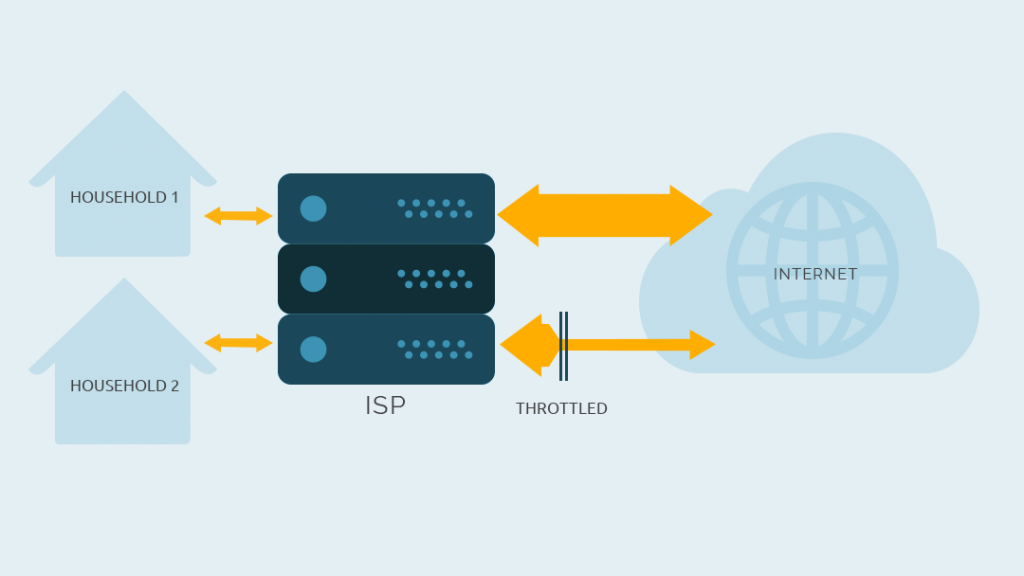
If you are using a VPN, the Internet Service Provider is not able to classify your traffic, so they cannot prioritize certain traffic. But elsewhere providers have throttled all OpenVPN traffic that runs over the UDP protocol. Switching to TCP helps in this case or some providers also offer OpenVPN via SSL, OpenVPN via SSH or OpenVPN via Tor or other connection options. Various VPN providers offer technologies for obfuscation. This masks the metadata of the OpenVPN protocol. In this case the provider does not see anymore that the data is VPN traffic.
By the way, throttling after the consumption of a permitted data volume has nothing to do with net neutrality. If you exhaust your data volume, you will not be able to reach full speed again even with a VPN.
You see all the benefits of a VPN, right?
Let’s recap. A VPN:
- Is good for privacy, data protection and anonymity.
- Prevents your Internet Service Provider and governments from snooping and spying on you.
- Protects you from hackers in foreign networks, public hotspots and Wi-Fi access points.
- Can protect you from malware and compromised DNS servers.
- Helps against the hated and annoying helps against the hated and annoying geoblocking.
Here’s a small additional tip: With a VPN you may even be able to save money. Some services set the price according to your location, or rather the location of your IP address. If you move your IP address to another country, you might get a better price for a hotel or your plane ticket might be cheaper. At this point, you just have to play around a bit and use the private mode of your browser to avoid cookies. Close the browser between the requests! Don’t you think so? Works for example also with Eurosport! Maybe more saving is possible with dialing into other countries, I haven’t tried that. I can prove it … 😉
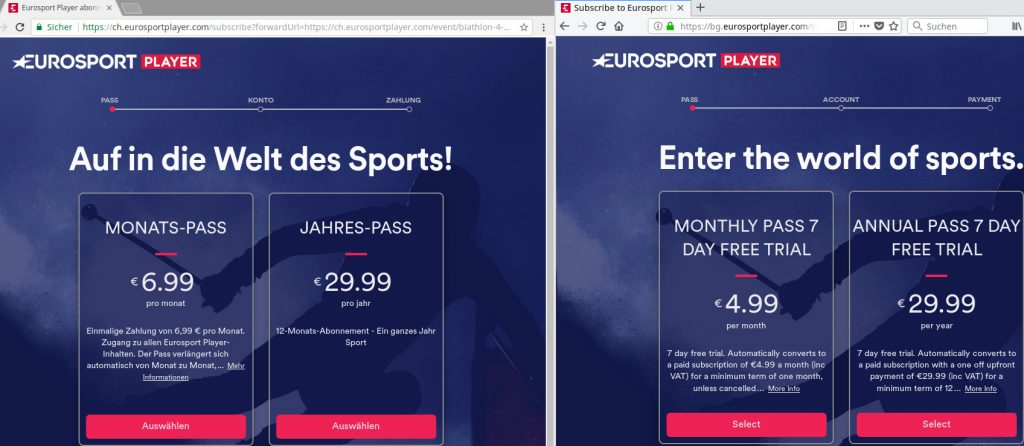
WOW! That must be expensive, huh?
No! The great thing is everyone can afford a VPN these days. There is something for every budget, depending on the use case. Some offer more functions or bypassing geoblocking is better, others simply serve to avoid prying eyes. I myself use NordVPN (big discounts NOW)* and [AirVPN] every day, as well as own solutions (sshuttle – very geeky) from time to time, because I run my own server. Your privacy is worth the few bucks.
Tip: With Linux I really like the WireGuard implementation of NordVPN, called NordLynx. It’s first class. WireGuard could well be the future of VPN, because the protocol is faster and easier than OpenVPN.
Hungry for some additional information? Excellent!
What is a kill switch and why is it important?
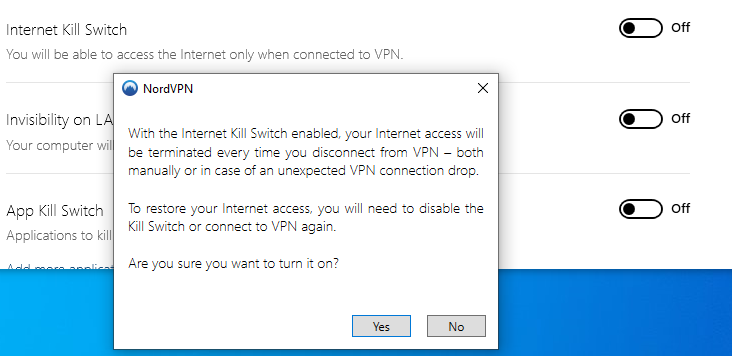
A so-called kill switch is a mechanism that immediately disconnects all network connections if the VPN connection is interrupted. The reason doesn’t matter. As soon as the VPN connection drops the kill switch terminates all traffic.
In case the VPN connection fails, your device would use the normal connection of the Internet Service Provider. As described above, data leaks would occur, or the ISP could track you and so on.
So the kill switch monitors whether the connection to the VPN server is active. If this is no longer the case, the function immediately cuts all connections. As soon as the VPN is up and running again, the kill switch is satisfied and opens the line. The clients and apps of many VPN providers include a function that automatically re-establishes a connection after a cut.
But check if you want to use the function. The kill switch is often deactivated by default. If you want to use this function, please check if it is active! In the following screenshot you see an example. It shows the settings of the Windows client of NordVPN.
Bypassing of firewalls is also possible
Almost all networks have a firewall and you have certainly heard the term before. With a firewall you can block certain ports and also other services. To do this, the firewall device must be able to examine your traffic. It’s actually a similar mechanism to that used by Internet Service Providers, if not the same.
As soon as you connect to a VPN and send all traffic through the VPN provider’s server, you have basically overridden the firewall. You can browse the internet without restrictions and censorship. As mentioned before, some firewalls try to block VPN traffic. Most of the time, you can get around such a restriction as well. A little trick might be to use a different protocol instead of a possibly blocked OpenVPN. Maybe a switch from UDP to TCP helps and so on. Some VPN providers offer certain mechanisms to hide VPN traffic from a firewall — I have already mentioned this. Some call it obfuscated servers, some stealth servers or hidden servers and so on.
What are the origins of a VPN?
Just a brief explanation. In the past, VPNs were primarily used by companies to connect two locations. Long cables do not work across borders and fixed lines are very expensive. Conventional Internet lines are much cheaper and you can use them as virtual, private lines. Of course the performance can suffer if I share the line with many others.
Nowadays, companies often use a combination of fixed lines (MPLS), Internet connections with VPNs and the so-called DMVPN (Dynamic Multipoint Virtual Private Network) is becoming more and more popular. With this technology you can set up connections between locations as required without having to go through a central office (hub-spoke network). Companies use SDN (Software-defined Network) and other technologies in corporate networks and large data centers to optimize traffic. If you are interested in these topics research them on the Internet. But the topic is very complex and would lead too far at this point.