To use your Raspberry Pi as a hotspot or access point is actually straightforward. You will find many guides that talk about lengthy manual configurations via command line with hostapd and so on. But it is actually much easier if you use RaspAP. Not only is the installation much easier – you also get a graphical interface (GUI) to manage your Wi-Fi hotspot or access point. Once this is done, you only need a few simple additional steps to turn your Raspberry Pi into a VPN router. RaspAP does work Raspbian Buster that I am using in this tutorial.
Quick guide how to use your Raspberry Pi as a VPN router
To use your Raspberry Pi as a VPN router seems to be more complicated that it actually is. In a nutshell those are the steps required:
- Install Raspbian Buster
Install Raspbian Buster onto your Raspberry Pi. I am using Raspbian Light as a graphical interface is not necessary.

- Get RaspAP
Get RaspAP up and running. This turns your Raspberry Pi into a Wi-Fi hotspot or access point.

- Get a VPN
Get a VPN that runs on Raspbian and ideally one with a command line client. I’m using NordVPN as it has one of the most versatile Linux clients on the market. You can try NordVPN as the service offers a 30-day money-back-guarantee. It is undoubtedly one of the best VPNs on the market. Try NordVPN 30 days without risk!*

- Install the VPN
Install the VPN on Rasbian and connect to a server.

- Enjoy your VPN router!
Quick Guide from the comments (thanks!)
Software changes and sometimes it gets easier. Thanks for this quick guide from a recent installation:
- Update the system and set Wi-Fi country (https://raspap.com/#manual-installation Prerequisites)
- Get NordVPN* and install the client (you might need to reboot here)
- Configure the client:
- Log in
- Whitelist ports 22, 67-68 (
nordvpn whitelist add portornordvpn whitelist add ports) - Switch to nordlynx (
nordvpn set technology nordlynx) - Deactivate NordVPN Firewall:
nordvpn set firewall off - Install RaspAP
- Configure RaspAP:
- Change SSID, password etc.
- Use NordVPN DNS addresses (103.86.96.100 and 103.86.99.100) in RaspAP to avoid leaks
- Restart
That is pretty straightforward and really worth a try.
Update: With Linux client 3.9.0 you can set the firewall on or off (nordvpn set firewall on/off). That might be helpful as well for your router.
If your connection does freeze once in a while – maybe that script helps:
! /bin/bash
PING="/bin/ping -q -c1"
HOST=example.com
${PING} ${HOST}
if [ $? -ne 0 ]; then
/usr/bin/systemctl restart nordvpnd.service
sleep 45
/usr/sbin/runuser -l pi -c 'nordvpn c UK'
fiPlease check HOST in case you want to ping something else. Also change the user after runuser -l – in my case that is pi because the script runs on a Raspberry Pi läuft. The script starts the MordVPN daemon new if the ping fails – after a certain waiting time it connects to the UK. Of course, you can change that as well.
Prerequisites for using RaspAP on a Raspberry Pi
For this to work, you need a Raspberry Pi with two network cards. One of them must logically be a wireless network card (Wi-Fi) because it serves as a hotspot or access point. The other network card could theoretically also be a wireless network card, but better is the integrated Ethernet interface. The Raspberry Pi 4 shown below also works, of course.
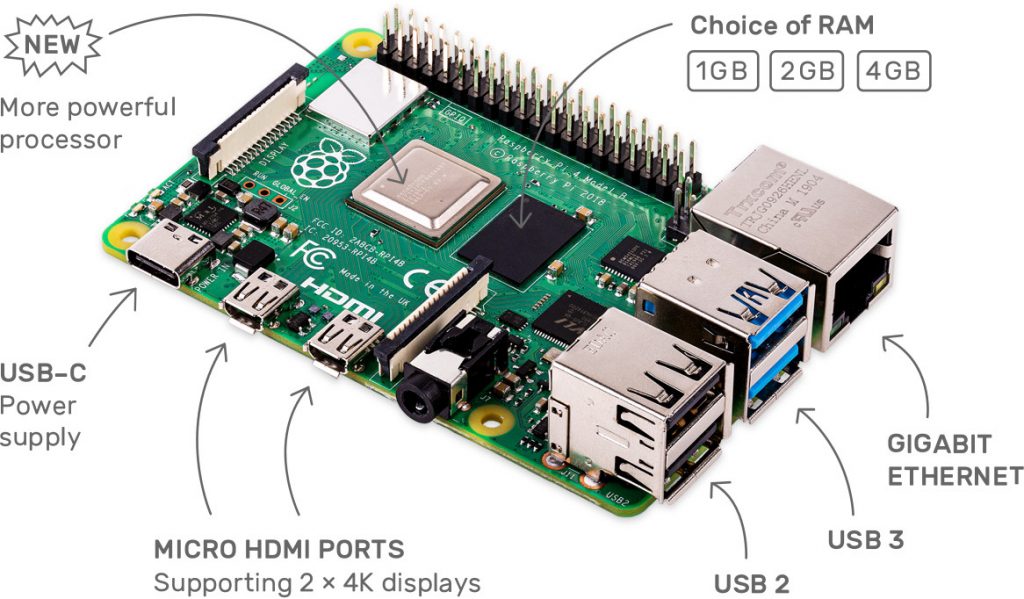
Let’s put it this way: The easiest way is to use a Raspberry Pi that already has an Ethernet and wireless interface. The Pi expert knows immediately that we are talking about the Pi 3 B upwards. For Pis without an integrated Wi-Fi card, it’s best to use a cheap, compatible USB network interface. I have had very good experiences with the Edimax. The cost is about 7 Euro.
Logically you need a suitable power supply, a microSD card and so on. With the microSD card a relatively small one is enough, but you hardly get anything under 16 GB these days. They only cost about 10 Euro — affordable so. You also need a network cable if you want to follow my instructions.
Mouse, keyboard and screen are not necessary! As already mentioned, I use Raspbian Buster as my operating system. But the lite version is enough for me, and we configure the operating system so that you can access it immediately via SSH.
Which Raspberry Pi should I use for the hotspot?
That’s a good question. The new Raspberry Pi 4 is powerful and works very well but it needs more power than its predecessors. If you don’t want to buy an additional network card, you can use both Pi 3 B and Pi 3+ B. The most energy saving would probably be a Raspberry Pi Zero W, if you extend it with an Ethernet interface. It might not powerful enough for a task like that but I didn’t test it to be honest.
My scenario
I tested RaspAP with a Raspberry Pi 3+ and used the integrated network interfaces. The Ethernet interface was connected to the router. This is my gateway to the Internet.
Install Raspbian Buster Lite on the microSD card
In the download area of the project page you can find the image for Raspbian Buster Lite. It has 426 MB and should be downloaded relatively fast.
Update: The Raspberry Pi Imager is a nice option to install Raspberry Pi OS Lite.
As soon as you have the image, you can upload it to your microSD card. I use Etcher because it’s the most convenient way. But also dd or other options are possible.
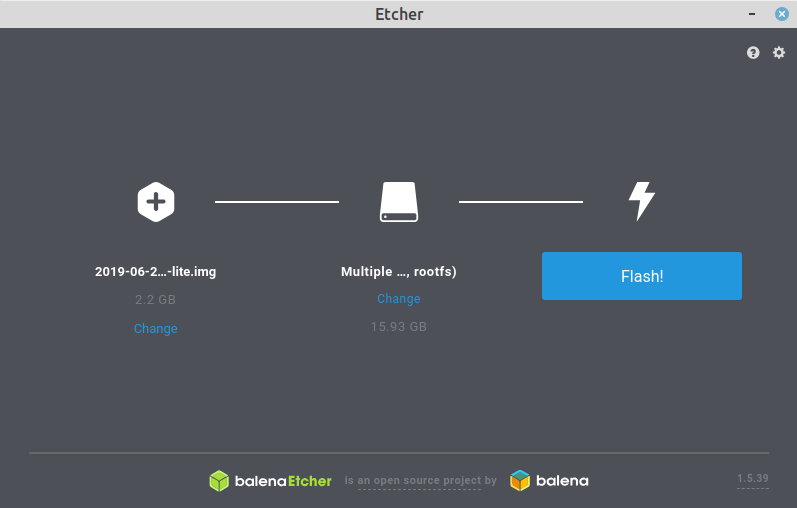
Depending on the OS and speed of the microSD card, the installation may take a while. Once the image has been installed, mount the microSD card again because we immediately prepare the operating system for remote access.
SSH access from the beginning
Simply create an empty ssh file on the boot partition without an extension. This is very easy under Linux. For example, the command touch ssh is sufficient. The boot partition looks like this afterwards:
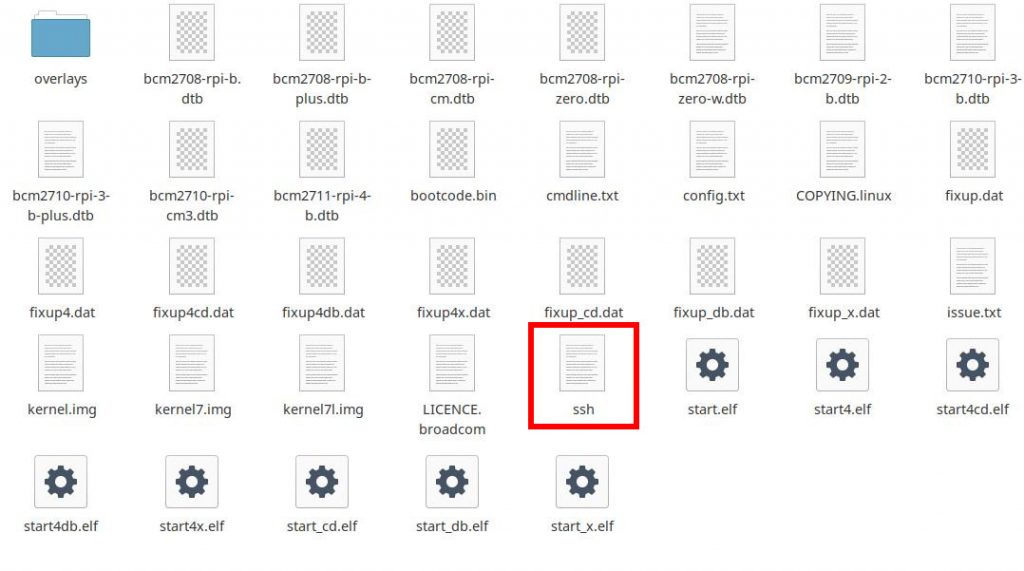
If the file ssh exists, Raspbian activates the SSH server at system startup and you can access the operating system via Secure Shell. This way you don’t need a screen, keyboard or mouse. If you connect the Pi to the router via the Ethernet network cable, no further configuration is necessary because the Pi is assigned an IP address by the DHCP server of the router.
It gets a little more complicated if there is no DHCP server in the network or if you want to use a wireless network card as gateway. As already mentioned, the Pi in my case uses a network cable.
Determining the IP address of the pi
If you have started the Raspberry Pi, then you find out the IP address. Usually it is enough to check the router. Most routers tell you which devices are within the network and which IP addresses have been assigned.
I like to assign static IP addresses to such devices. Normally, you can assign an IP address to a MAC address in the DHCP server of the router. This way the Raspberry Pi always gets the same IP address and you don’t have to configure it within the operating system. Another advantage of this method is that the DHCP server does not assign the IP address to any other device. DNS servers and so on are also assigned to the PI by the router.
As soon as you know the IP address, remote access should be possible. In my case, the IP address was 192.168.1.2. By default, the name and password of the SSH access on a Pi are: pi and raspberry:
ssh pi@192.168.1.2On first access you have to confirm that access is really granted.
As soon as you are logged on to the Raspberry Pi, you should change the password for the user pi immediately, otherwise everyone in the same network can get access to your device. Either you use the command passwd or you open the Pi configuration:
sudo raspi-configThis opens the command line configuration tool.
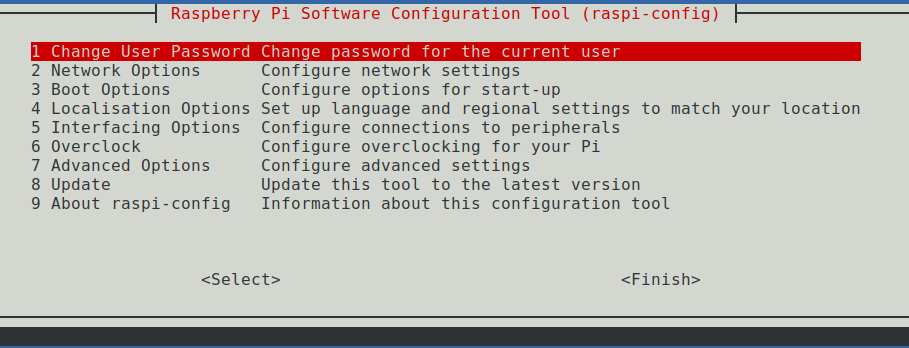
Because the configuration tool is already open, you can also set the country settings right away — if necessary:
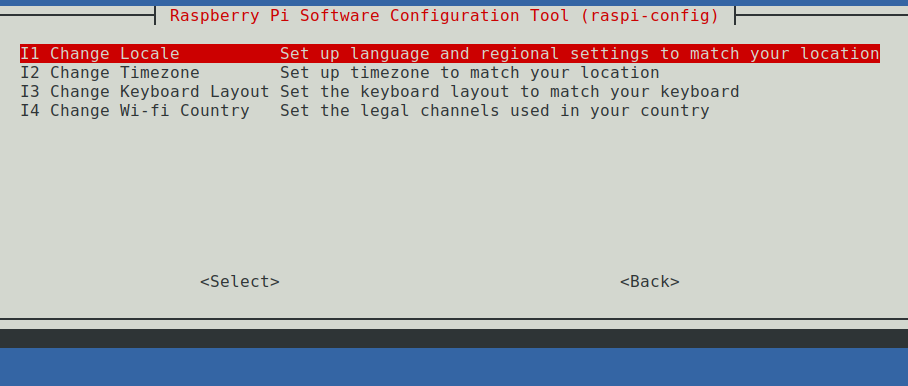
Update Raspbian Buster straight away
It is also advisable to update the system. An upgrade never hurts and Raspbian know the drill anyway:
sudo apt update
sudo apt dist-upgrade
sudo rebootNow you need to restart the device before you continue. After that, you have to reconnect to the Pi via SSH. Once the operating system Raspbian Buster is updated and the system restarted, we can convert the Pi into hotspot with RaspAP.
Installing RaspAP – step by step
Now we install RaspAP. The project page can be found at raspap.com. We don’t have to visit it directly, but it doesn’t hurt to know the source. If you are logged in on your Pi, you install RaspAP just like that:
wget -q https://git.io/voEUQ -O /tmp/raspap && bash /tmp/raspapThe installation is starting now:
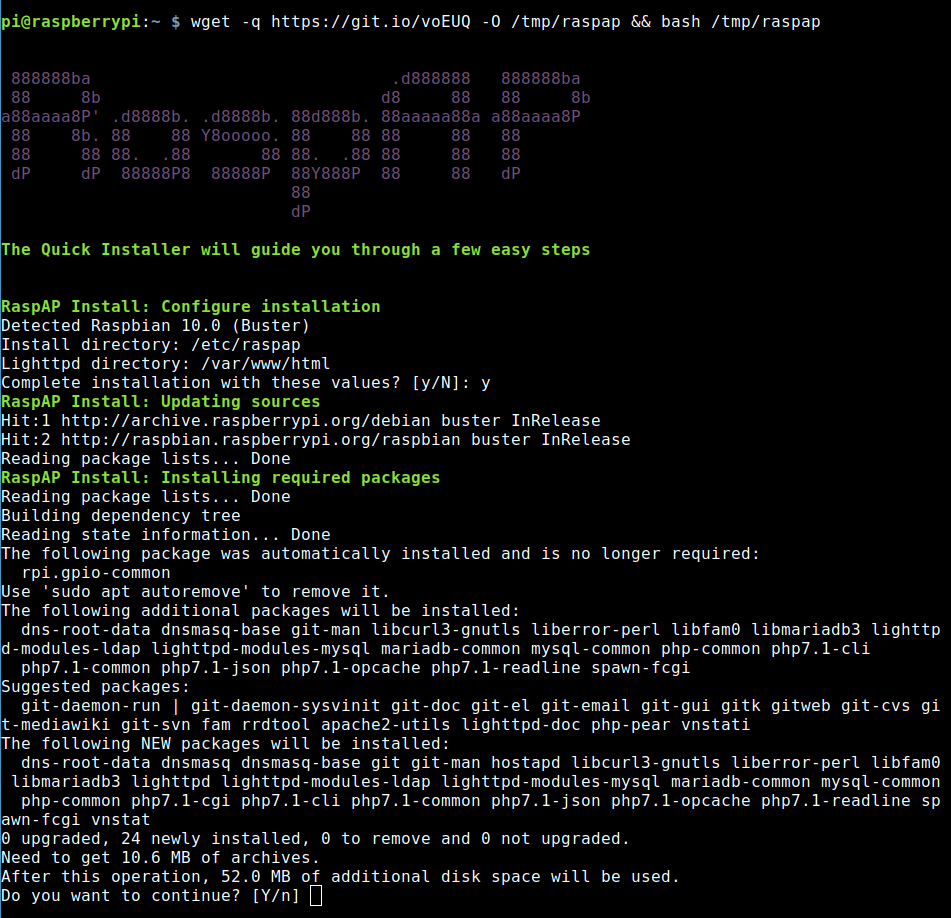
During the installation I had to answer a few questions, which I answered with Yes: http-cookies -> Yes – Control service -> Yes
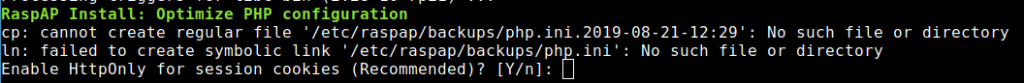
Furthermore, the system asks if you want to install the ad blocker and the OpenVPN client. I installed both. The functions don’t hurt, and you don’t have to use them if you don’t want to.
That’s all and it! RaspAP is installed on your system!
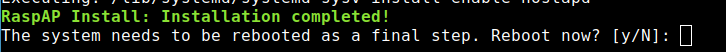
As you can see in the screenshot, the system wants to restart. So, we do RaspAP the favor.
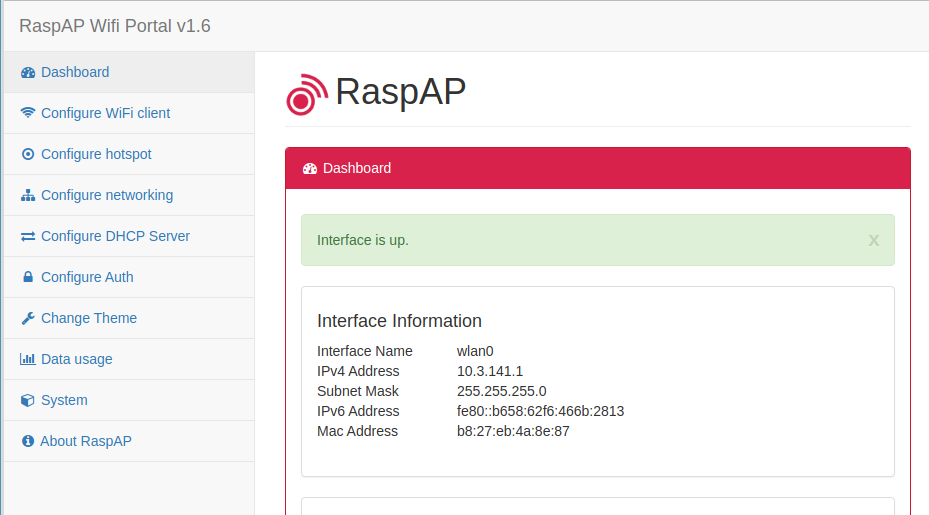
IP address of RaspAP or the hotspot
By default, the hotspot gateway has the IP address 10.3.141.1. This is fine because it does not interfere with the other 192.168.1.x network. I have not changed anything at this point. As DHCP area RaspAP is preconfigured with 10.3.141.50 to 10.3.141.255.
By default RaspAP has the name raspi-webgui as SSID and the password is ChangeMe. The hotspot or access point is now ready for use and you can log in. You can change the password and SSID in the web GUI if you want.
Here is what you need to know as the default settings:
- IP address: 10.3.141.1
- Username: admin
- Password: secret
- DHCP range: 10.3.141.50 — 10.3.141.255
- SSID: raspi-webgui
- Password: ChangeMe
RaspAP’s web gui
You configure your hotspot completely via your browser. Either you log in to the hotspot and use URL 10.3.141.1 or you are in another network and open the admin interface with (in my case) 192.168.1.2.
By default, you log in with admin and secret. At this point I would advise you to change all passwords first and adapt the hotspot to your needs. You can also configure the DHCP server via the web GUI. Here are some screenshots, how it looks like.
Under Configure hotspot -> Basic you can configure how the Pi hotspot should be found. In my case I changed it to pi-hotspot for example.
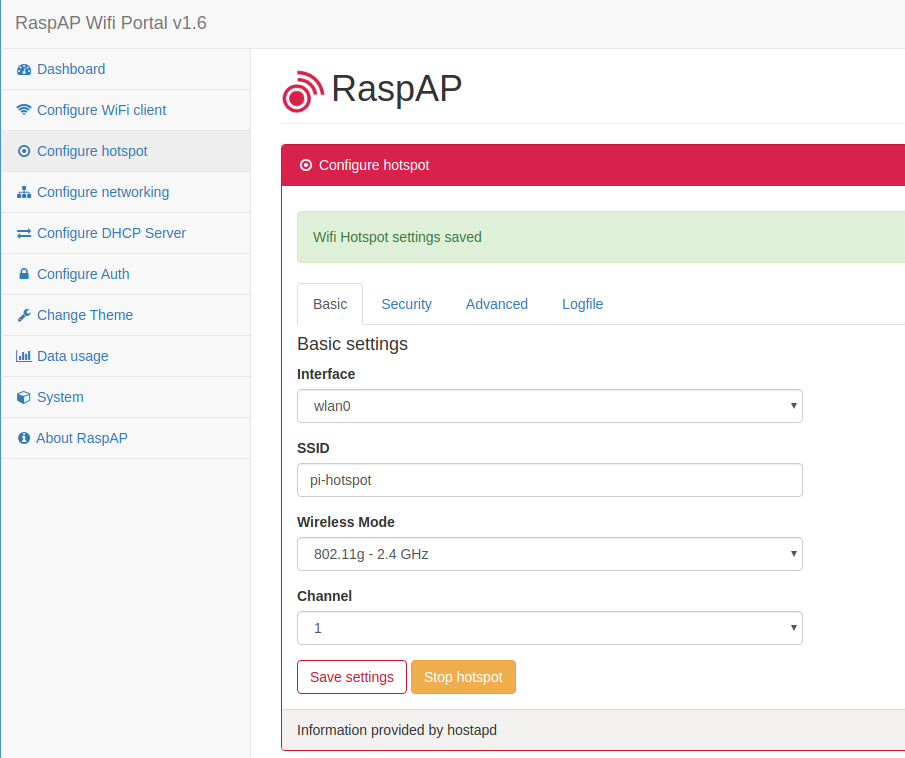
That works and I can connect:

A ping to my website confirms to me that I can access the internet via RaspAP.
You change the password for the hotspot under Configure hotspot -> Security. Maybe you want to change Security type to WPA + WPA2.
The settings or the DHCP server are under Configure DHCP Server:
In most cases you don’t have to change these settings.
More settings for RaspAP
The hotspot software also offers a console.
However, it is only of limited use, since it does not give you root access and you cannot switch with sudo. I would leave that as is and manage the operating system exclusively via SSH.
You don’t like the theme? Change it! There are a few other options like a terminal theme.
if you open the Dashboard you always see the most important settings straight away.
As you can see, the installation of RaspAP is simple. But basic knowledge of networks in general is helpful.
Changing the DNS server of RaspAP
Update: In more recent installations of RaspAP you can set the DNS addresses within the GUI. There is no need to do it via command line if you prefer a graphical interface.
By default, RaspAP uses 1.1.1.1 (Cloudflare) and 8.8.8.8 (Google) as DNS servers. The DNS servers are stored in the file /etc/dhcpcd.conf.
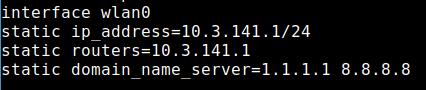
If you want to use your own, change this here. Maybe you have the adblocker Pi-Hole in your network and RaspAP should use it as DNS server. FreeDNS is also a nice alternative.
Your Raspberry Pi is now a working Wi-Fi hotspot or access point. Now we will turn it into a VPN router. Did you already register with NordVPN?
Once you have RaspAP installed and running, take the next step and build your own VPN router. These are just a few additional steps. In this article, I’ll explain step-by-step how it works.
VPN router only counts as one device!
Many VPN providers allow the use on a router and your Raspberry Pi will only count as 1 device or 1 connection, no matter how many smartphones, tablets and computers are connected to it.
That is a nice advantage if you ask me. Furthermore, you can use it as a Wi-Fi access point for devices where no VPN client does exist for. Connect your Chromecast to the VPN router, your Smart TV, your gaming console and so on.
A VPN router is also an excellent choice if you want to connect a Kodi device to it. LibreELEC is a very nice operating system if you want to install Kodi on a Raspberry Pi. But there is no easy way to use VPN apps for Kodi or LibreELEC. However, you could connect your LibreELEC device to your VPN router and circumvent the issue.
Don’t forget the rise of IoT (Internet of Service) devices! A lot of them will connect to Wi-Fi but have very limited options to install additional software. For a lot of those devices the only option to use a VPN is a VPN router.
If your Raspberry Pi acts as a VPN router you don’t need to install a client on every device you want to use the VPN. Just connect the Pi to the server or country you want to use and connect the devices to the Pi. It really is that simple.
So let’s get started and turn the Raspberry Pi into a VPN router.
Do all VPNs work?
In theory any provider that provides ovpn files works. This allows you to connect to the provider manually via the OpenVPN protocol. First, I’ll show you how to use the Linux client from NordVPN to build a VPN router as this is the most convenient way. After that I’ll tell you how it works with a normal OpenVPN connection.
Install NordVPN on the Raspberry Pi and turn it into a VPN router
If you want to follow my instructions, you need a subscription to NordVPN. It’s great that the VPN provider offers a 30-day money-back-guarantee. You can first try out whether your Raspberry Pi runs properly as a VPN router and if not, you simply demand your money back. The provider doesn’t ask stupid questions and usually refunds rapidly.
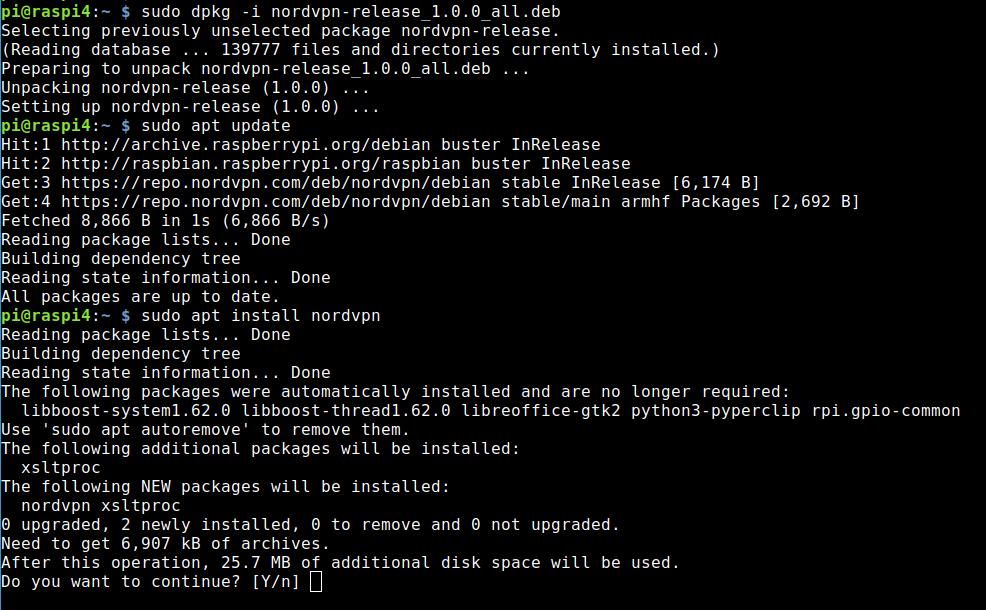
My Raspberry Pi runs headless — without peripheral devices like screen, mouse and keyboard. I log on to the device via SSH. After that, I download the deb file from NordVPN.
wget -c https://repo.nordvpn.com/deb/nordvpn/debian/pool/main/nordvpn-release_1.0.0_all.debNow you install the file via shell:
sudo dpkg -i nordvpn-release_1.0.0_all.debThe deb file is basically only setting up the repository. You have to update the package information and after that you install the Linux client of NordVPN.
sudo apt update
sudo apt install nordvpnIt looks like this:
Setting up the NordVPN client
The first step is to log on to the client with your access data from NordVPN:
nordvpn loginNow the client asks for username and password.
The Linux client of NordVPN provides a so-called Whitelist. I put port 22 here to be on the safe side so that SSH access is possible in any case.
nordvpn whitelist add port 22You can review the settings with the following command:
nordvpn settingsQuick connect to NordVPN work like that:
nordvpn cImportant! Now the Raspberry Pi does not work anymore as a hotspot or access point! If you are still connected to the Pi hotspot, you won’t feel a difference. But new connections are impossible — so we need to fix that.
NordVPN changes iptables on our VPN router (if the firewall is on)
The reason for the behaviour is that the Linux client of NordVPN modifies iptables — if the firewall is not deactivated. I recommend deactivating the firewall because it saves a lot of hassle.
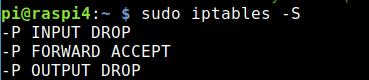
If you want to proceed with the firewall active here are a few hints and tips. You can view the current rules with that command:
sudo iptables -SIf you do that before and after a connection to the VPN you see what I mean:
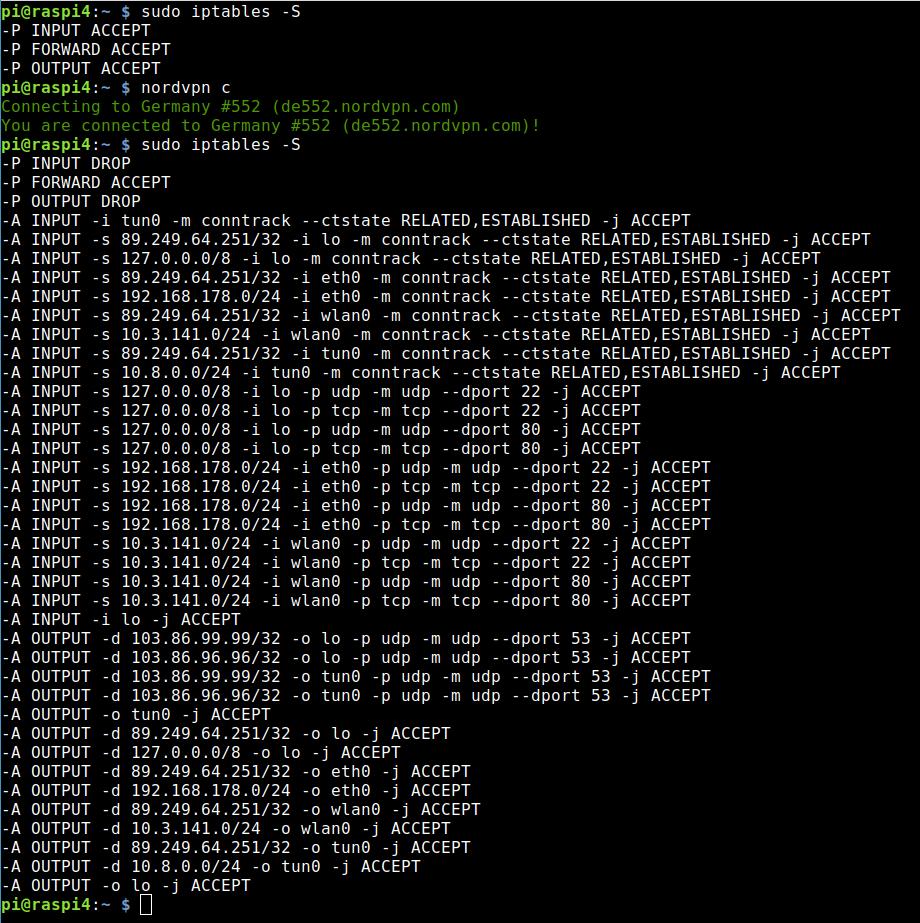
If I want to connect to the Pi Hotspot now, I don’t even get an IP address anymore. That’s why I execute the following two commands and the hotspot assigns me an IP address again and works as designed:
sudo iptables -P INPUT ACCEPT
sudo iptables -P OUTPUT ACCEPTHowever, the device does not route my traffic to the Internet. Therefore, the following iptables entries are necessary.
sudo iptables -t nat -A POSTROUTING -o tun0 -j MASQUERADE
sudo iptables -A FORWARD -i tun0 -o wlan0 -m state --state RELATED,ESTABLISHED -j ACCEPT
sudo iptables -A FORWARD -i wlan0 -o tun0 -j ACCEPTNow everything works as designed — but there still is a little catch.
Making the settings for VPN router permanent
With the commands shown above, the settings are only temporary. They are lost as soon as you restart the Raspberry Pi. The first two commands will also be overwritten when you connect to another NordVPN server.
Now there are several options to make the settings permanent. Of course, I want NordVPN to connect to the startup immediately. A cronjob via /etc/crontab is an option. For this, I first create a script file, which I simply call nordvpn.sh.
nano nordvpn.shI put the following lines into it:
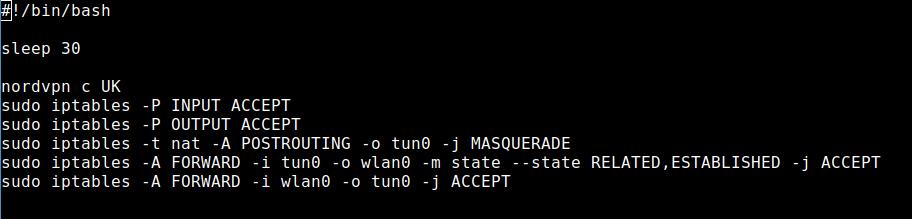
I need the line sleep 30 because the NordVPN daemon needs a bit after the system starts and the command
nordvpn c UKwould not be executed. As you can imagine, that command would connect me to a server in the UK. In this case you would be able to stream BBC iPlayer for example.
I tried with sleep 20 and sometimes it worked — sometimes it didn’t. So, I opted in for a 30-second wait and that is OK. The file need to be executable as well.
chmod +x nordvpn.shNow I put the following line at the end of the file /etc/crontab:
@reboot pi /home/pi/nordvpn.shIt looks like this now:
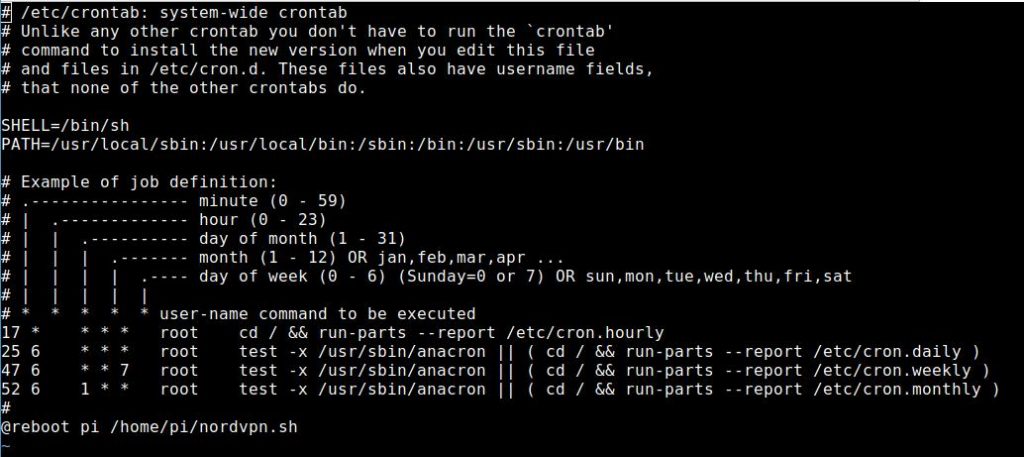
Tip: If you want to execute the script via /etc/rc.local be aware that the user pi has to run the command. The login data of NordVPN are stored per user and that is in this case pi. Per default the user root will be in charge of the file rc.local!
su pi -c '/path/to/script'The above command would execute the file as user pi.
Connect automatically to the VPN – VPN router has to be reconfigured
It is possible that the connection to the VPN fails – that happens once in a while. In this case, the data traffic of your device would no longer be routed through the VPN. We want the VPN to reconnect automatically in case of a connection failure. You can do this with the command:
nordvpn set autoconnect onThis would also automatically connect the VPN client when the device is restarted. However, the iptables entries are missing and therefore I run my script once the system starts.
You can also specify a country with autoconnect:
nordvpn set autoconnect enabled UKThe software would connect you automatically to the UK.
What happens if the connection goes down?
I disconnected the router from the Internet (pulled the cable) and waited a minute to see what happens. After plugging the cable back in, the DSL line first synchronized and shortly afterwards the Internet connection was restored.
My VPN router still worked as before. If you want to be on the safe side, you could run another mini script every minute as a cronjob. For example, call the crontab as user pi:
crontab -eand use a line like that:
* * * * * /home/pi/nordvpn-minute.sh > /dev/null 2>&1If everything is fine, the script has no effect. If the VPN connection is established, it will not be re-established. In case the iptables settings are correct, the system will not overwrite them. The output of the cronjob is transferred to /dev/null (digital black hole).
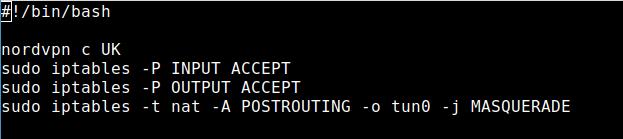
The reason for the script is clear. If the VPN daemon connects completely new, it sets INPUT and OUTPUT to DROP and our hotspot doesn’t work anymore.
Yeah, it’s not the most elegant method but it seems to work reliably. I have tried it. If you run the command via cronjob, you don’t have to worry about it at startup. At the latest one minute after the NordVPN daemon is available, a connection to the VPN is established.
You may even want the VPN router to stop working if it fails. This would also be a kind of kill switch and you can see what went wrong.
In the end, you’ll have to experiment a bit to see which solution works best for you. But with a little patience, trial and error, your VPN router will be up and running in no time.
Tip: If your client cannot connect to the Wi-Fi hotspot with the VPN activated try to add ports 68 and 69 UDP (DHCP) to the whitelist.
nordvpn whitelist add ports 68 69 protocol UDPThen try again — maybe with a restart in between. As mentioned at the start you can also try to deactivate the firewall (from NordVPN Linux client 3.9.0 on:
nordvpn set firewall on/offA few thoughts regarding the VPN router
You may want to restart your VPN router once a day. You could also do that with a cronjob.
If you disconnect the VPN connection and then log in again, you might get a faster server assigned.
A web GUI where you can enter the country you want to connect to would be pretty fancy. Maybe that is a project you want to do afterwards. Shouldn’t be too complicated to be honest but you need a web server installed.
OpenVPN – connect the VPN router via ovpn file
Most good VPN providers provide ovpn files so you can set up an OpenVPN connection manually. Clients have the advantage that you can change the country more conveniently. The client of NordVPN has another advantage. You can use CyberSec and the obfuscated servers. CyberSec is a neat feature because it blocks ads, tracker, and malware. Every device that is connected to the VPN router will benefit from CyberSec! The obfuscated servers also known as stealth servers are nice in countries with strong censorship. They might help to beat geoblocking from streaming providers as well.
A connection via ovpn file has the advantage that the hotspot works as designed without any problems. The command does not add any new iptables rules at all.
Install OpenVPN
For this to work, you have to install OpenVPN on the Raspberry Pi:
sudo apt install openvpnThen get the ovpn file you want. To stick to the NordVPN example, you will find the OpenVPN configuration files for all servers on this page. The list is quite long and if you’re looking for a particular server, the page with all the servers is more convenient.
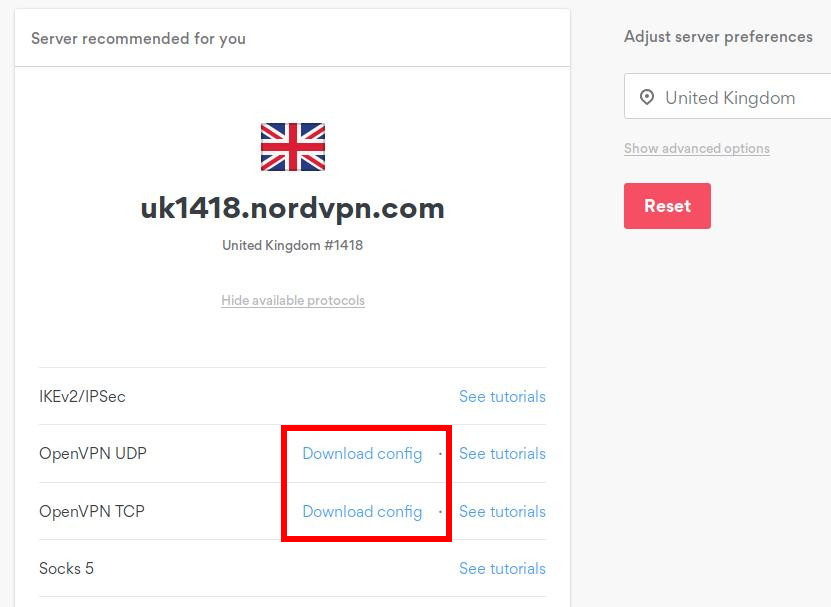
Just with that file you already can establish a connection. If you installed the OpenVPN client for RaspAP you can use the backend to import your .ovpn file.
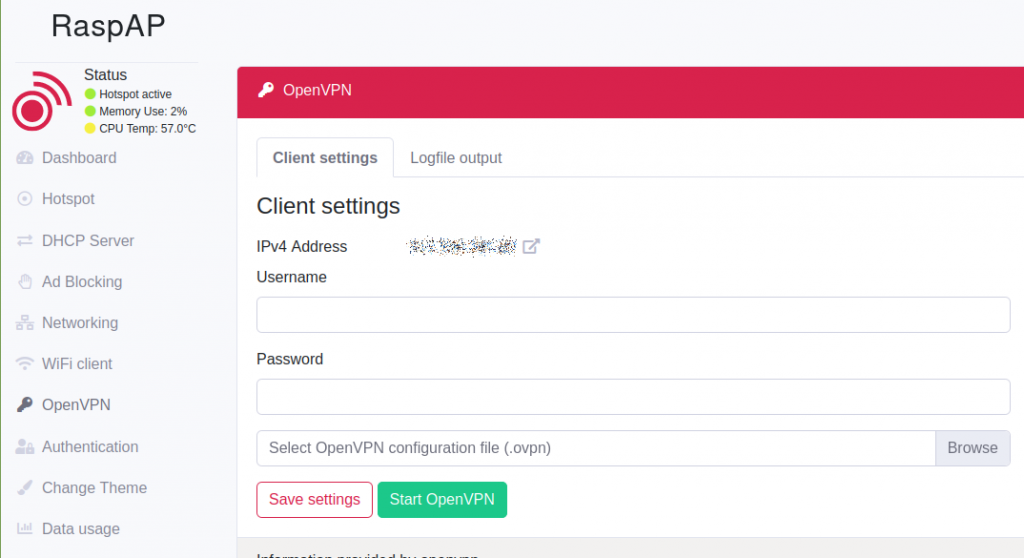
Of course, you can do this manually.
sudo openvpn uk1418.nordvpn.com.udp.ovpn &Now you have to enter Username and Password. That should be the case with most VPN providers.
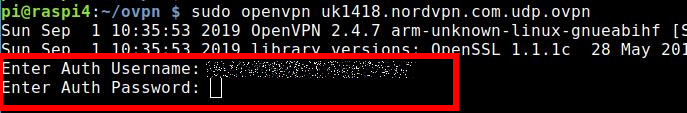
It’s OK for a test but you can’t connect automatically like that. If you want to do that, you need a file e.g. auth.txt. It hast to be in the same directory as the ovpn file.
The first line holds the Username and the second line is the Password!
Then enter or modify the following line in your ovpn file: auth-user-pass auth.txt
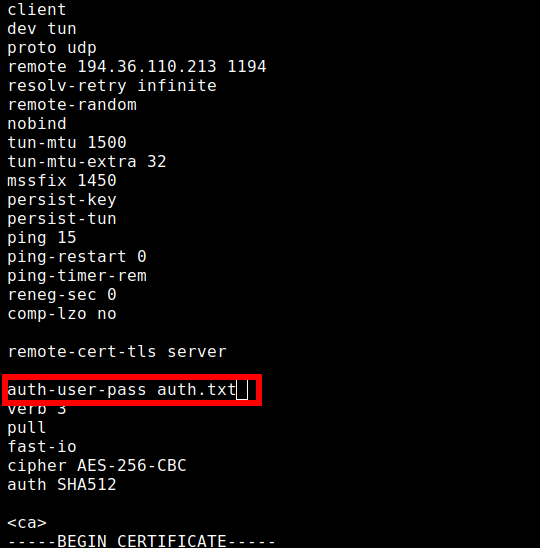
If you use the OpenVPN command from above again, your system automatically logs on to the VPN server. Now you can also automate the process.
Be careful! DNS leak!
However, you will continue to use the DNS servers of the hotspot. If you have not changed them, they are the 1.1.1.1 (Cloudflare) and 8.8.8.8 (Google) defined by RaspAP. You can find them in the file /etc/dhcpcd.conf. The static IP address of wlan0 is stored there as well by the way.
This is basically a DNS leak. With my solution and the client of NordVPN I also use the DNS servers of the VPN provider and therefore my DNS queries are anonymous.
Of course, you can also solve this differently. Maybe you have a Pi-hole in the network anyway and use it as DNS server. There are many possibilities here, including FreeDNS. I just wanted to point out the potential DNS leak here.
In the DHCP configuration of your RaspAP you can also define what DNS servers the clients should get. Use the DNS servers of NordVPN to avoid leaks: 103.86.96.100 and 103.86.99.100
Does that also work with NordLynx (WireGuard)?
If you have installed a current client, NordLynx also has a uniform network interface. It is called nordlynx. Here is a screenshot:
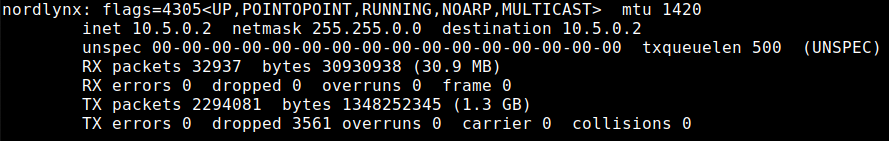
Now I can make the corresponding routing entries. WireGuard is slightly faster than OpenVPN and it’s your decision what you want to use. The solution with OpenVPN as VPN router works very well and that is not a slow either.
However, the solution for the network interface nordlynx for iptables looks like this:
sudo iptables -t nat -A POSTROUTING -o nordlynx -j MASQUERADE
sudo iptables -A FORWARD -i nordlynx -o wlan0 -m state --state RELATED,ESTABLISHED -j ACCEPT
sudo iptables -A FORWARD -i wlan0 -o nordlynx -j ACCEPTWould you like to make your own VPN router now? It’s really not difficult and NordVPN is a good partner for it.
As I said, most reputable VPN providers should provide the resources for your project. I like NordVPN because I can use the command line client under Linux. But the provider also provides a great Android client. It is one of the most user-friendly providers on the market.
With NordVPN you can use up to 6 devices simultaneously. Because a VPN router is allowed, your Raspberry Pi counts as 1 device, no matter how many others are connected to it.
The VPN provider also allows torrent downloads and P2P connections / file sharing.
Jon
says:HI,
Firstly thanks for the fantastic guide.
Just one question…I have followed you guide and everything is working well, however I am now looking to route traffic from my second wired connection (eth1) via the VPN as well as the traffic from my wireless access point (wlan0). Is this possible with raspap? if so how? Or can you point me in the right direction? Should I be bridging eth1 and wlan0 then setting up the new bridged network adapter name to route via the VPN (just like we did for wlan0 in your guide)? Many thanks
Jon
says:Apologies I just saw Simon’s question on 24th August 2021 at 5:03 am…pretty much covers it…however just a thought…
In your response you say that eth and wlan would be on different networks, could you then use raspap’ s bridged ap mode to use dhcp from you main router and consolidating the networks? hmmm
guyfawkes
says:Worth a try … I haven’t tested that to be honest … but in this case, you wouldn’t need the hotspot at the Raspberry Pi if your normal Wi-Fi is within reach. All you have to do is using the Raspberry Pi as a gateway and the traffic will be routed through the VPN. Basically, you could configure the DHCP on your router to use the IP address of the Raspberry Pi as the gateway.
Mark Sherwood
says:Hi there
I’m getting a Segmentation fault when running this on a Raspberry Pi 2b. The exact image works on my 4b. Has anyone seen this and what can I do to fix it?
Thanks
Mark
guyfawkes
says:The 4B is 64-Bit, the 2B might not be – depending on the model … that might be the cause of the error …
T
says:Hi Fawkes, this might be the only tutorial on the entire internet that goes into details and actually makes it work. But still Im hitting a roadblock somewhere. I do every step as written (openvpn option, lynx option, whitelisted ports etc)
I either get wifi with no connection with vpn on, or I get (at best) few seconds of wifi connection with VPN on before AP on rasp crashes – and nothing can connect until I restart hostap.
my steps: restart hostap, connect vpn, let something connect raspi wifi, do 3 iptables commands. wifi dies or is just offline
Im desperate at this point with rasp. do I need to forward some ports on router or something?
and as added bonus giving nordvpn creds+ovpn file to RaspAP does absolutely nothing and hotpost stays offline.
guyfawkes
says:Is the firewall option in the NordVPN off?
Do you have the option to try different hardware? It’s a shot in the dark, but it might be a hardware problem.
Really difficult to analyse the problem from remote — I am using exactly the setup I described here, and it works.
ShadowRyze
says:Hi @guyfawkes!
Great and clear tutorial!
I wanted to do something very similar but I am a complete Linux novice and was hoping you could help me?
Through trial and error, I have discovered that my TV services only work when using NordVPN obfuscated servers.
I was thinking of getting a small travel router with OpenVPN to connect my TV (no WiFi) to these NordVPN obfuscated servers, however after asking NordVPN how to set that up, they mentioned that obfuscated servers are only available within the NordVPN app.
It was suggested to me to buy a Raspberry Pi and use the NordVPN client on there to share the connection with my TV.
However, I am a complete novice and don’t know how to do that.
I assume it would be quite similar to this tutorial, but I was hoping to do it in an opposite direction (taking WiFi and sharing it via Ethernet – instead of taking Ethernet and sharing it via WiFi).
I was hoping if you could provide me with a mini tutorial of what I need to do here?
I’ve never owned or set up a RPi before, but I can follow some of the instructions you’ve written in this tutorial as guidance but I’m stumped at other points.
Thanks for any help you can give!
guyfawkes
says:The just release Raspberry Pi Zero 2 W might do the trick nicely. For a travel router you probably would need a second Wi-Fi card — a USB Wi-Fi card that basically replaces the Ethernet card in my setup. All you have to do while travelling is connect the gateway Wi-Fi card to the wireless LAN you want to use. The rest should be identical to the tutorial here.
Long story short — yes, it’s a matter of replacing the Ethernet interface with a second Wi-Fi interface.
Doug
says:I have pi-hole and pi-vpn installed and running well. Addtionally, I’m running cloudflared and sending DNS queries over https. However….
I want to be able to run ExpressVPN using an openVPN client on my laptop and still send the DNS Queries to my Raspberry Pi running Pi-hole. I have an Open VPN client app that has the option to over-ride the server suggested VPN. I have been NOT been able to get this to work. I think it’s because when I start the VPN on my laptop it is on a different subnet (10.x.x.x.x) than my client PC (192.168.xxx.xxx) and I need some sort of routing rule.
My Requirementsa. I want all my traffic to be encrypted and anonymous b. I want to be able to turn off and on my client side VPN if a site doesn’t work with the VPN , without breaking PI-Hole (I want Pi-hole for the ad-blocking)c. I don’t want to use the PI as a VPN gateway for all my network traffic. ( I use split tunneling for specific apps on the client side. I think server side VPN would be too limiting for my purposes)d. I want to be able to change my client side VPN location
My Thinking1. Run Express VPN on my Client PCs2. Run Express VPN on my Pi-Hole Server3. Be able to turn on and off the VPN on my Client PC, but still have the routing to Pi-Hole work
Questions:1. Is my thinking reasonable, or is there a better/different way to accomplish my requirements.
2. How do I do it? I’m new to linux and need some specific help in identifying the exact routing rules, where to edit them and the exact IP values I need to use (again I’m using OpenVPN on both sides. I want it to work when both VPNs are running as well as when either VPN is turned off)
guyfawkes
says:Doesn’t work with newer clients of ExpressVPN because they set force_vpn_dns to true, and you cannot deactivate it. Meaning – as soon as you activate the Linux client on your Desktop you cannot reach your Pi-hole. However, I haven’t tried running ExpressVPN on a Pi-hole server … I don’t use it because I can’t configure my own DNS servers and because it is now part of Kape Technologies – former the adware / malware distributor Crossrider – too many red flags for me.
Furthermore, from my long years of IT experience I normally live with compromises instead of trying to create a “jack of all trades”.
NordVPN you can use Pi-hole as you can set the DNS server yourself, or you simply use CyberSec as that is the built in ad blocker … if you would use that on your “VPN Raspberry Pi router” with activated CyberSec or a Pi-hole and another VPN on your client … you are pretty much where you want to be – if I did understand you correctly.
Mark
says:This is a great guide! I’m 90% there. However I don’t use Nord. I have a custom Wireguard server in another country that I’m trying to connect to but I’m unsure how to configure iptables.
I’ve installed RaspAP. I can connect to the RaspAP access point and browse the internet.
I’ve installed Wireguard on the Pi and have it set up as a peer. I’ve confirmed the Wireguard is connected by running the command…
host myip.opendns.com resolver1.opendns.com | grep “myip.opendns.com has” | awk ‘{print $4}’
… which reports that the IP address is now located in the other country.
I’m stuck at how to configure iptables (including what exactly goes into script that’s run by cron, including if this is where I launch Wireguard).
Your guide below mentions nordlynx as the interface, but again I’m not using that and I’m not very familiar with iptables. I ran your iptables commands (replacing nordlynx with wg0) and it worked, but it didnt survive a reboot and now no longer works. I’m at a loss.
I’m also unsure when to run wireguard – is this run from the cron script, and if so, how?
The RaspAP documentation gives a hint as to what to use at https://docs.raspap.com/wireguard, but it also mentions PostUp and PostDown needs configuring yet doesn’t say a damn thing about what actually is needed. But maybe I don’t need that because I’m not interested in using it as a server, but as a client so I can watch foreign TV from my Apple TV.
Any help is appreciated.
Mark
says:PS – Ugh this all posted as one large paragraph. I submitted it as separate paragraphs. Sorry.
guyfawkes
says:The iptables command was only necessary because the NordVPN client changed some settings. In your case, this part might not be necessary at all. You might need to allow the port you are using for your WireGuard connection – default is 51820 UDP.
The WireGuard connection you could automatically start with systemctl enable wg-quick@wg0 for example (where wg0 is the name of your connection – might be different in your case) … but that depends a bit on the Linux distribution you are using.
Mark
says:You’re right! I tried again with a fresh install of Raspian Bullseye lite. I installed RaspAP with default settings, then installed Wireguard and configured it in a basic peer mode. Once I brought the interface up, the wireless access point switched to the foreign IP address. Nothing more is needed! I didn’t do anything to the Pi firewall either. Thanks for your help!
I do have a question though. In the RaspAP installation log, it said “Adding rule: -t nat -A POSTROUTING -j MASQUERADE
Adding rule: -t nat -A POSTROUTING -s 192.168.50.0/24 ! -d 192.168.50.0/24 -j MASQUERADE”
What does this do? I’m curious specifically because of the subnet address in mentions. Is this detecting my subnet? Or is this RaspAP creating a subnet to use for its own purposes?
If this is RaspAP creating a subnet from scratch then this is a concern because my LAN subnet address is EXACTLY THE SAME! And if that’s the case I’m worried about conflicts between the two.
I noticed that exact same subnet address (192.168.50.0) on the screenshot of your RaspAP install log >> https://vpn-expert.info/wp-content/uploads/2020/01/raspap-installation-control-service.png
So either by random chance you have the same less common subnet address as me (I chose mine because it seemed a little different from the usual 192.68.0.1, etc), or this is RaspAP creating one that the devs assume is a little different so as to not conflict with the more common ones. If that’s the case, how do I change the RaspAP one?
guyfawkes
says:That is basically routing the traffic from the RaspAP Hotspot (Wi-Fi) to the other network interface (Ethernet) … if the NAT rule (Network Address Translation) would not be there no traffic could flow from one subnet to the other – because Wi-Fi and Ethernet should be on different subnets a rule must allow the traffic exchange between them.
192.168.x.x is a private subnet and everybody can use it internal without creating a conflict on the internet. I think you are right that RaspAP picked this one not to create a conflict in internal LANs. But it’s easy to change and wouldn’t make a difference, I guess.